Difference between revisions of "Lesson 54--Microduino MD5"
(Created page with "{| style="width: 800px;" |- | ==Purpose== This course will show you the most common MD5(Message Digest Algorithm 5) and explain the correctness of encryption in Microduino. ...") |
|||
| Line 78: | Line 78: | ||
Step 3: | Step 3: | ||
| − | + | ||
[[File:MicroduinoMD5_1.jpg|600px|center|thumb]] | [[File:MicroduinoMD5_1.jpg|600px|center|thumb]] | ||
Revision as of 01:10, 30 May 2016
PurposeThis course will show you the most common MD5(Message Digest Algorithm 5) and explain the correctness of encryption in Microduino. 本教程将介绍如何使用最常用的加密方法MD5加密,并在Microduino中解释加密的正确性。 MD5 EncryptionIntroduction:' MD5 is a widely-used hash function in the field of computer safety, offering overall protection for information. The file number of the algorithm is RFC 1321. ( R.Rivest,MIT Laboratory for Computer Science and RSA Data Security Inc. April 1992) Here is the brief introduction of MD5: MD5 handles the input information grouped in 512-bit and each group is divided into sixteen 32-bit group. After a series of processing, the output of the algorithm consists of four 32-bit groups which generates a 128-bit hash value after cascading. Advantage: Van oorschot and Wiener has considered to find brute-force hash function and they supposed a specially designed MD5 conflict searching machine can find a conflict every 24-day. But from the year of 1991 to 2001, there was no new algorithm that came to replace MD5. From that we can see, MD5 is not influenced in safety. All the defects cannot become the problem of MD5 in practical application. Besides, since MD5 algorithm needs no copyright cost to pay, it can also be treated as an excellent intermediate technology. Disadvantage: On August 17th, 2004, Chinese professor Xiaoyun Wang posted the decode of MD5, HAVAL-128, MD4 and RIPEMD algorithm in Crypto’ 2004 in the US, announcing the decoding result of MD series algorithm. (Note: it was not really decode but accelerated hash collisions.) Equipment
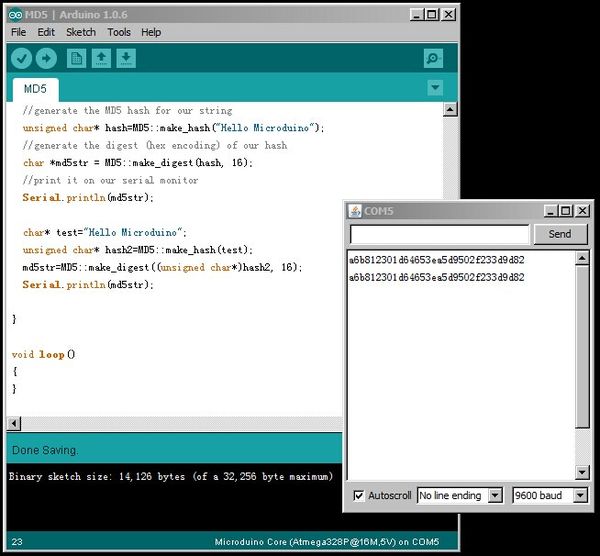
Program#include "MD5.h"
/*
This is en example of how to use my MD5 library. It provides two
easy-to-use methods, one for generating the MD5 hash, and the second
one to generate the hex encoding of the hash, which is frequently used.
*/
void setup()
{
//initialize serial
Serial.begin(9600);
//give it a second
delay(1000);
//generate the MD5 hash for our string
unsigned char* hash=MD5::make_hash("Hello Microduino");
//generate the digest (hex encoding) of our hash
char *md5str = MD5::make_digest(hash, 16);
//print it on our serial monitor
Serial.println(md5str);
char* test="Hello Microduino";
unsigned char* hash2=MD5::make_hash(test);
md5str=MD5::make_digest((unsigned char*)hash2, 16);
Serial.println(md5str);
}
void loop()
{
}DebuggingStep 1: Download the code and run it. If the compile goes wrong, it means you don’t have local library of [ArduinoMD5]. After download and installation, you should restart IDE.
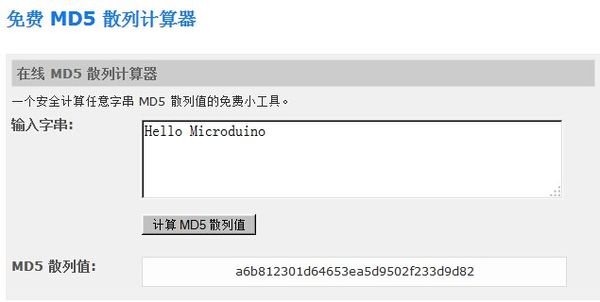
The ciphertext is the text after “Hello Microduino” gets enciphered by MD5.
The result is consistent with the calculation result of the editor on the online MD5 website. ResultThe text “Hello Microduino” is enciphered by MD5 algorithm, which is very hard to be changed to the previous one. Video |